A crucial component of any IT architecture is network devices, often known as network infrastructure devices. Network devices facilitate connectivity and communication between people, devices, apps and the internet similar to how the nervous system manages all body impulses between important organs. They include wireless access points, switches, routers, firewalls, and integrated access devices. In this post we’ll discuss endpoint management and security for network devices and the best tools available to keep your network devices secure.
Importance of Vulnerability Scanners for Network Devices
It may be assumed, given their significance, that those network devices undergo the same level of maintenance as other systems or servers. But the truth is exactly the reverse. System administrators frequently hold off on making changes to network devices because they worry about the expensive downtime that may result from doing so. These changes are intended to improve the security posture of network devices. It’s more likely that these devices will become attack vectors because there are no standard tools available to monitor them.

These network devices are viewed as excellent targets by malicious cyberactors, who are frequently fast to spot setup errors. The majority of businesses have this equipment, which gives attackers more motivation to target them. Through the use of these devices, an attacker may obtain access to all data and traffic travelling through a network, bringing down the organisation’s entire IT infrastructure by executing lateral movement assaults. The fact that the attacks might be recurring is the worst aspect. Even if the IT staff take corrective action to stop and clean up after the assaults, the focus is largely on workstations, leaving the threat actors free to lurk in the network devices and wait for another chance to attack.
Firmware vulnerabilities should be given the same priority by organisations as software vulnerabilities by putting in place a reliable vulnerability assessment and patching methodology for network devices, the network is protected from firmware vulnerabilities as well.
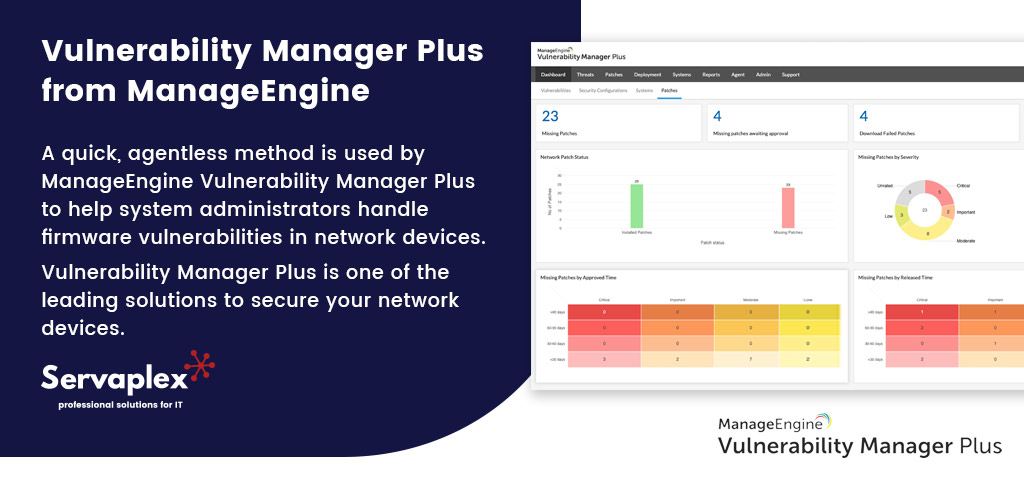
Vulnerability Manager Plus from ManageEngine
A quick, agentless method is used by ManageEngine Vulnerability Manager Plus to help system administrators handle firmware vulnerabilities in network devices. Vulnerability Manager Plus is one of the leading solutions to secure your network devices. There are three phases to strengthen network device security:
1. Discover the Network Devices
The first step in enhancing the security of the network devices used by the entire business is to create a centralised inventory. The Nmap scan is run by Vulnerability Manager Plus to find network devices. By first identifying the local office or remote office that the device is a part of, followed by either an IP address or the IP range of the whole network, devices that need to be managed may be found and added. The IT administrator can choose and add the relevant devices to the Managed Devices list once all network devices have been found.
2. Scan for Firmware Vulnerabilities
The next step is to specify the information needed for the devices’ scan after they have been found and added to the management system. In order to advance the scanning process, Vulnerability Manager Plus runs the scan without the use of an agent and needs the controlled devices’ credentials to access their data.
3. Remediate and Manage Vulnerabilities
We can aggregate the identified network devices to speed up the process before remediating and managing the vulnerabilities. Discovered devices must be grouped in this manner because firmware patch deployment strategies can only include devices from the same manufacturer, OS, and series as simultaneous targets.
Firmware Patches
By installing the most recent patch or stable firmware version, vulnerabilities in the firmware are fixed. The three phases in this technique are as follows:
- Upload the Firmware Patch
The first step in fixing the vulnerability is uploading the most recent patch or stable firmware version. The vulnerability’s patch or firmware version information will be made accessible, along with a download link from the vendor’s website. It must then be posted to the Vulnerability Manager Plus server after being downloaded. The integrity of the submitted patch may be verified using the checksum information given. - Choose Targets
The vulnerable hardware that applies will be automatically chosen for deployment and shown below. The chosen targets can be changed to satisfy the requirement. - Configure Deployment Settings
It is possible to arrange deployment to occur automatically or at a specific time. All flaws in the system are fixed by updating to the most recent firmware version.
Note: Vulnerability Manager Plus currently supports patching only for network devices that run the Cisco and Juniper OS.

The All In One Vulnerability Scanner
IT administrators no longer have to switch between several security products thanks to Vulnerability Manager Plus. It offers software vulnerability assessments, patch management, CIS compliance, security configuration management, web server hardening, and high-risk software audit capabilities in addition to network device vulnerability scanning and management in the same console to ensure centralized, seamless management.
ManageEngine Vulnerability Manager Plus Trial
When you download a fully complete, 30-day trial edition of ManageEngine Vulnerability Manager Plus, you can get a 360-degree view of your security posture. If you any questions about the product then give us a call now on +353-1-2304242 or contact us online to speak to a specialist.
If you have an IT Problem then we’ve got the IT Solution, call us on +353-1-2304242 or contact us online for more info!




