What is Security?
The term IT security also called cybersecurity is applied to technology and computer systems. describes techniques that secure information processing systems. It focuses on protecting computers, networks, programs and data from unauthorised access or damage. against attack scenarios, to avoid economic damage and to minimize risks.
Three basic security concepts important to information on the internet are confidentiality, integrity, and availability.
Concepts relating to the people who use that information are authentication, authorization, and nonrepudiation.
IT Security Products

Log management, auditing, and IT compliance management for SIEM
If you want to know what’s happening in your network to gain insights into potential threats and stop them before they turn into an attack, then you need to investigate your logs.
Log-generating aspects of an enterprise’s network
All these components generate an immense volume of log data. Manually sifting through logs from all these sources to find security events of interest, such as user accesses, unusual activities, user behaviour anomalies, policy violations, internal threats, external attacks, data theft, and more, is futile.
EventLog Analyzer Available In 3 Editions

Password Manager Pro is a secure vault for storing and managing shared sensitive information such as passwords, documents, and digital identities of enterprises.
Password Manager Pro Benefits
What Problems Does Password Manager Pro Solve?
Administrative/Privileged passwords are literally aplenty in enterprises. Servers, databases, switches, routers, firewalls and any other hardware or software, could have equally large number of administrative passwords. These passwords are insecurely stored in spreadsheets, text files and even as printouts and are shared by a group of administrators.
This traditional practice brings with it a host of issues such as:
Password Management Features Matrix
Standard Edition
• Centralized password vault
• Manual resource addition
• Import resources from CSV files
• Import resources from KeePass
• Import resources from active directory
• Password policies
• Password sharing and management
• Audit and instant notifications
• User / User group management
• Local authentication
• RADIUS authentication
• AD / Azure AD / LDAP integration
• Export passwords for offline access
• Password reset listener
• Backup and recovery provisions
• Remote RDP, SSH, and Telnet sessions
• Two-factor authentication – OTP sent via email
• Rebranding
• Mobile access (Android, iOS, Windows)
• Browser extensions (Chrome, Firefox, IE)
• VNC support for collaboration
• Transfer approver privileges
• IIS AppPool password reset
• IIS Web.Config discovery
• Password protected exports
• Backup file encryption
• IP restrictions- Web access
• Managing unidentified email addresses
• Emergency measures
• Personalization of user interface(Night-mode theme)
• Notification Email IDs
Premium Edition
• All Features of Standard Edition
• AD / Azure AD Sync – User groups & OUs
• Auto Logon Helper
• Password access control workflow
• Admin dashboard (Live feeds, reports and graphs)
• Password action notifications (Resource group-specific)
• Remote Password Reset (On-demand, Scheduled, and Action-based) – List of supported platforms
• Agent-based password reset
• Canned reports
• Two-factor authentication – PhoneFactor, RSA SecurID, Google Authenticator, Duo security, YubiKey, Microsoft Authenticator,Okta Verify
• High availability
• Privileged session recording
• AD / Azure AD Sync – User groups & OUs
• Password management API (XML RPC, SSH CLI)
• Privacy settings
• Password reset plugin
• User Sessions
• Trash Users
• IP Restrictions – API access and Agent Access
• Disable Password Resets for Privileged Accounts
• Password Reset using SSH Command Sets
Enterprise Edition
• All features of Premium edition
• Data Encryption and Protection with SafeNet HSM
• MS SQL server as backend database
• Privileged accounts discovery
• Active directory sync – resources
• LDAP Sync – User and User Groups
• SAML 2.0 support
• Remote SQL sessions with auto logon
• Role customization
• Ticketing system integration-ServiceDesk Plus On-Demand, ServiceDesk Plus MSP, ServiceDesk Plus, ServiceNow, JIRA Service Desk
• Custom password reset listeners
• Scheduled export of encrypted HTML files
• SIEM integration – SNMP traps & Syslog messages generation
• Email templates for notification configuration
• Landing Server Configuration
• Federated Identity Management
• Smart Card / PKI / Certificate Authentication
• Two-factor Authentication – RADIUS
• Custom Reports
• Out-of-the-box compliance reports (PCI DSS, NERC-CIP, ISO/IEC 27001, GDPR)
• SQL query reports
• Privileged session shadowing and termination
• SQL server failover clustering
• RESTful API
• Encryption key rotation
• EAR support while using MS SQL as backend database
• Purging selective session recordings
• File transfers over remote desktop sessions
• Secure cloud storage options
• CI/CD Platform Integration – Jenkins, Ansible, Chef, Puppet

“Log analytics and configuration management software for network security devices”
Gaining network activity insights and keeping abreast about firewall log is a challenging task as the security tool generates a huge quantity of traffic logs.
Introducing Firewall Analyzer, an agent less log analytics and configuration management software that helps network administrators to understand how bandwidth is being used in their network. Firewall Analyzer is vendor-agnostic and supports almost all open source and commercial network firewalls such as Check Point, Cisco, Juniper, Fortinet, Palo Alto and more.
Firewall Analyzer Benefits
What Problems Does Firewall Analyzer Solve?
This traditional practice brings with it a host of issues such as:
Firewall Analyzer Features Matrix
Standard Edition
Supports up to 60 Devices
Network Traffic Analysis
• Bandwidth Reports
• Inbound / Outbound Traffic
• Internet / Intranet Reports
• VPN Usage & Trend
• Protocol Usage
• Firewall Rules Report
• Sites Accessed by Users
• Firewall Device Audit Report
Network Security Reporting
• Attack / Virus Reports
• Spam Reports
• Failed LogOn Events
• Denied Events & Websites
• Insider Threat Reports
Dashboard
• Custom Dashboards
• User Specific Dashboards
Alert Management
• Criteria based Real-time Alert
• Network Behavioural Anomaly Alert
• Interface Bandwidth Utilization Alert
Forensic Analysis
• Incident Analysis with Raw data
• In-depth auditing with aggregated database entries
User Management
• Local Authentication
General
• Failover/High availability (as addon)
• Network Troubleshooting Tools
Professional Edition
Supports up to 60 Devices
Firewall Rule Analysis
• Policy Overview
• Policy Optimization (Anomaly Detection)
• Rule Cleanup
• Rule Reorder & Recommendation
• New Rule Impact Analysis
Firewall Configuration Analysis
• Real-time Change Notification
• Historical Configuration Change Tracking
• Regulatory Compliance (ISO, PCI-DSS, NERC-CIP, SANS, NIST)
• Security Audit Report
• On-demand Configuration Backup
Dashboard
• NOC/SOC View
• Embed Widget
User Management
• AD Based Authentication
• Radius Authentication
• Pass Through Authentication
• REST API Access
General
• Failover/High availability (as addon)
• Rebranding
• Diagnose Connections
• Multi-Language Support
+ All the features of Standard Edition
Enterprise Edition
Supports up to 1200 Devices
• Scalable architecture
• Monitors multi-geographical locations
• Distributed central-collector architecture
• Site specific reports
• Web-client Rebranding
• Client & user specific views
• Failover/High availability (Default addon)
+ All the features of Professional Edition
Privilege misuse is a top cybersecurity threat today that often results in expensive losses and can even cripple businesses.
It’s also one of the most popular attack vectors among hackers, because when successfully carried out, it provides free access to an enterprise’s underbelly, often without raising any alarms until the damage is done.
“Minimize security risks. Maximize business value.”
ManageEngine PAM360 empowers enterprises looking to stay ahead of this growing risk with a robust privileged access management (PAM) program that ensures no privileged access pathway to mission-critical assets is left unmanaged, unknown, or unmonitored.
PAM360 is a comprehensive solution for businesses looking to incorporate PAM into their overall security operations. With PAM360’s contextual integration capabilities, you can build a central console where different parts of your IT management system interconnect for deeper correlation of privileged access data and overall network data, facilitating meaningful inferences and quicker remedies.
PAM360 Benefits
M365 Security Plus
“Secure and protect Microsoft 365With M365 Security Plus”
Manage engine Security for M365 is powered by Microsoft’s Enterprise Mobility + Security (EMS).
Microsoft EMS provides your organization with a platform to protect against advanced threats, personal data loss and unauthorized access into the environment as employees become more mobile.
“An exclusive solution to fortify Microsoft 365 environments”
M365 Security Plus Solutions Offered
M365 Security Plus Services Supported
How does M365 Security Plus stand out from the rest?
“Securely manage and store your logs on our cloud platform”
Log360 Cloud is a cloud-based log management solution for managing and storing logs from your IT infrastructure.
This solution allows security teams to manage their logs from the cloud, helping them achieve their IT security and compliance objectives.
How does it work?
Your network logs help you detect, investigate, and mitigate security incidents. Securely manage and store your logs with ManageEngine’s Log360 Cloud. Don’t let security incidents go unnoticed.
“Secure log management from the cloud”
Why should you consider Log360 Cloud?
Log360 Features
Log Management
• Log Management for Network Security
• Event Log Management
• Syslog Management
• Event Log Auditing
• Unix Auditing and Reporting
• Linux Auditing and Reporting
• Windows Device Auditing
IT Compliance Reports
• Compliance Audits
• PCI Compliance Reports
• ISO 27001 Compliance Reports
• FISMA Compliance Reports
• HIPAA Compliance Reports
• SOX Compliance Reports
• GLBA Compliance Reports
• Reports for New Regulatory Compliance
• Customizing Compliance Reports
• GDPR Compliance Handbook

DataSecurity Plus is a data visibility and security solution that offers data discovery, file storage analysis, and real-time Windows file server auditing, alerting & reporting.
Furthermore, it monitors file integrity; streamlines compliance requirements; generates instant, user-defined email alerts; finds sensitive personal data (PII/ePHI) stored in files, folders, or shares; and automatically executes predefined responses when security threats such as ransomware attacks occur.
DataSecurity Plus caters to any organization that’s looking to enhance data visibility, strengthen its security, and streamline compliance for file servers.
ManageEngine DataSecurity Plus Features
DataSecurity Plus is Available in 3 Editions

Patch Manager Plus, our all-around patching solution, offers automated patch deployment for Windows, macOS, and Linux endpoints, along with patching support for 900+ third-party updates across 500+ third party applications. It’s available both on-premises and on the cloud.
Features of Patch Manager
One-stop solution for multi-OS patch management
Patch Manager Available In 3 Editions

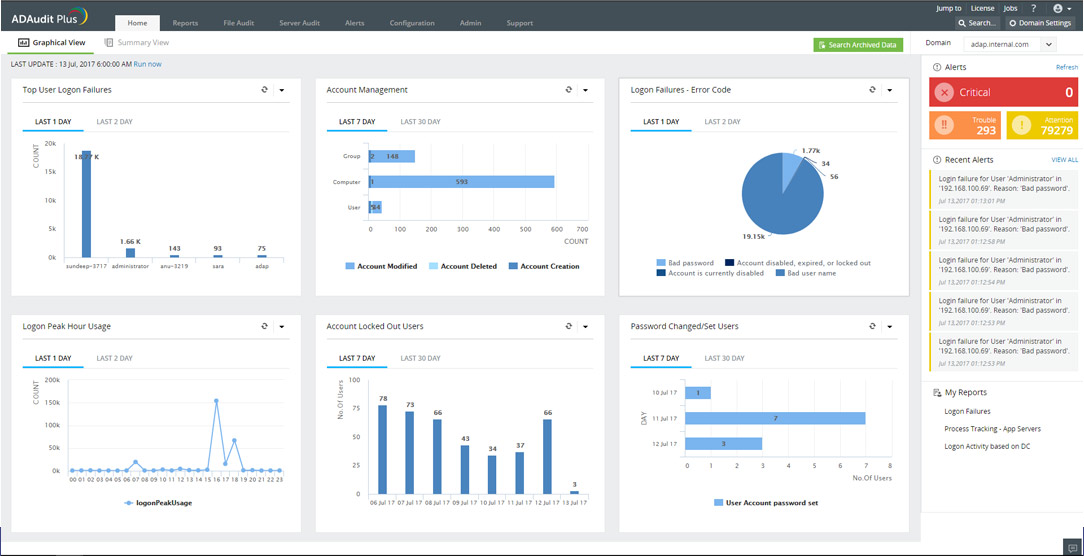
ADAudit Plus transforms raw and noisy event log data into real-time reports and alerts, enabling you to get granular visibility into Windows server activities with just a few clicks.
Monitors your Active Directory (AD), Azure AD, Windows file servers, member servers, and workstations, and help you adhere to regulations such as HIPAA, GDPR, SOX, CCPA, GLBA, and more
What does ADAudit Plus do?
Available In 2 Editions

Vulnerability Manager Plus is a multi-OS vulnerability management and compliance solution that offers built-in remediation. It is an end-to-end vulnerability management tool delivering comprehensive coverage, continual visibility, rigorous assessment, and integral remediation of threats and vulnerabilities, from a single console.
Whether your endpoints are on your local network, in a DMZ (demilitarized zone) network, at a remote location, or on the move, Vulnerability Manager Plus is the go-to solution to empower your distributed workforce with safe working conditions
Vulnerability Manager Plus Features
Vulnerability Manager Plus Available In 3 Editions
ManageEngine Device Control Plus
With any removable device such as USB, data theft is a one-step process: plug it in.
ManageEngine Device Control Plus is a comprehensive device control and file access management solution that allows you to control, block and monitor USB and peripheral devices from having unauthorized access to your sensitive data.
ManageEngine Device Control Plus Features
Vulnerability Manager Plus Available In 3 Editions

M365 Manager Plus is an extensive Microsoft 365 tool used for reporting, managing, monitoring, auditing, and creating alerts for critical activities.
With its user-friendly interface, you can easily manage Exchange Online, Azure Active Directory, Skype for Business, OneDrive for Business, Microsoft Teams, and other Microsoft 365 services all from one place.
M365 Manager Plus provides exhaustive preconfigured reports on Microsoft 365 and helps you perform complex tasks including bulk user management, bulk mailbox management, secure delegation, and more. Monitor Microsoft 365 services around the clock and receive instant email notifications about service outages. M365 Manager Plus eases compliance management with built-in compliance reports and offers advanced auditing and alerting features to keep your Microsoft 365 setup secure.
M365 Manager Plus Features
M365 Manager Plus Available In 3 Editions
Enterprise
• Supports 25 to unlimited number of users/mailboxes.
• Annual or perpetual subscription.
• Supported features:
• 500+ reports on Microsoft 365 services.
• Microsoft 365 auditing and alerting.
• Microsoft 365 health monitoring.
• Microsoft 365 management
• Password expiry notification
• Help desk delegation.
Starts at $595
See how your business can benefit from having your Endpoint Management looked after by the Irish experts. Give us a call now on +353-1-2304242 or fill in the form below and a member of our team will be in touch!