“In the age of the cloud, protecting enterprise data.”
The manner that businesses manage, access, and keep their data has changed thanks to the cloud. It offers several advantages, including affordability, scalability and accessibility making it the chosen option for many Irish businesses. However, since cloud services are used more often, businesses now face fresh security issues that can’t be solved by conventional security measures and this is where The Mitre Corporation is trying to make a difference. In this post we’ll discuss what Mitre are doing to help keep sites safe.
ATT&CK Matrix by Mitre
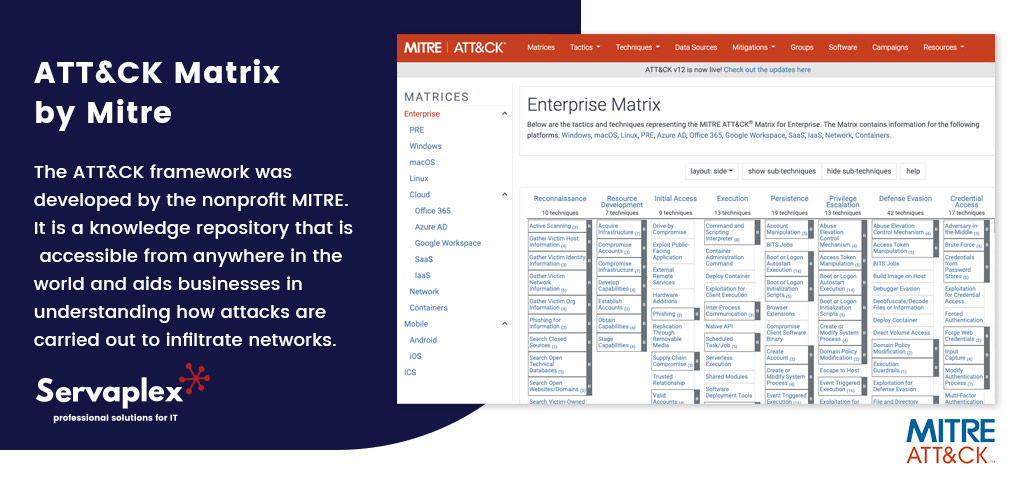
The ATT&CK framework was developed by the nonprofit MITRE. It is a knowledge repository that is accessible from anywhere in the world and aids businesses in understanding how attacks are carried out to infiltrate networks.
This architecture was developed after a thorough examination of actual cyber attacks, and it tries to build a network of allies for businesses to use in their fight against them. To keep up with the evolving cybersecurity scene, the framework is often updated with fresh and reliable inputs.
ATT&CK Meaning
“ATT&CK” is an acronym for Adversarial Tactics, Techniques and Common Knowledge. The 14 ways described in the MITRE matrix stand for numerous technological goals that an attacker may try to accomplish on a network of an organisation, and that is precisely what it is built of.
MITRE Strategies
The strategies outlined in the matrix begin with reconnaissance of the target’s domain and end with impact (consequences that could disrupt the normal functioning of a business). The strategies mentioned in the matrix define what an attacker could do to achieve a given “tactic”. The sub-techniques outline how a technique is carried out. An attacker need not try each of the strategies outlined in the framework. Their objective could be to employ the fewest possible strategies in order to succeed.
An enemy could carry out any approach in a variety of ways. Techniques are the various methods for carrying out a specific tactic. Each tactic may be associated with one or more techniques.
Techniques Used by Attackers
Here we discuss few prominent techniques employed by attackers.
- Spear Phishing Links: According to Verizon’s 2021 Data Breach Investigation Reports 5, spear phishing URLs included in email attachments continue to be a popular tactic for attackers to deceive employees into installing malware.
- Drive-by Downloads: Another method used for gaining initial access is drive-by downloads, in which staff members click on a link to download spyware without understanding the repercussions after being forwarded to a malicious website.
Detection of an Attack Using Log360
There are several steps involved in identifying an intruder using Log360, so let’s go through each method one by one.
- Defense Against Initial Access: Setting up intrusion detection systems (IDS) to recognise URLs from malicious sites is one of the detection and mitigation strategies recommended by the MITRE ATT&CK architecture against initial access. 5 IDS also looks for malicious patterns in system processes and checks system files against malware signatures to find attempts to infiltrate the network. Alerts are provided to the SOC and the intruder is removed from the network if any malicious behaviour is found.
“How log360 may be really useful here!”
ManageEngine Log360 gathers and examines log data and offers a number of pre-built reports that assist in monitoring login and logoff sessions as well as newly generated accounts in the domain. Additionally, you may see information from several IDS suppliers. These reports provide a comprehensive picture of the assaults taking place on the network, the devices that are being attacked the most, their frequency, and their origin. Additionally, Log360 is connected with threat feeds based on STIX and TAXII that may detect any traffic coming from dangerous URLs.
- Defense Evasion: An attacker concentrates their efforts on evading detection and getting past defences after breaching a network. As a result, the attacker has some time to move laterally throughout the network and gradually obtain access.
An attacker might use a variety of tactics to avoid protection measures. The difficulty in identifying an attacker resides in protecting the network from an invisible force.
- Defense Against Defense Evasion: If an organization’s security policy does not include endpoint monitoring tools, an attacker may be able to block network traffic that contains reports of endpoint activity. This method seeks to suppress signs that can warn security experts of a potential invasion.
Security analysts may clearly comprehend all actions taking place at your network endpoints with the aid of Log360. To assist you in auditing many sorts of system events on your Windows and Linux systems, it offers a broad variety of reports and warnings. Additionally, it may be integrated with a variety of endpoint security products, including well-known antivirus programmes, threat detection programmes, and vulnerability scanners. These reports of various types may be seen by security experts from a single console.
- Protection Against Command and Control: Every business must have a software usage policy that specifies the types of software that employees may or may not install. Organizations may use Log360 to audit endpoints for all software installs and updates, allowing them to keep track of compliance with these standards. Additionally, you may keep an eye on how whitelisted programmes are running and get updates on application crashes and issues.
- Defense Against Lateral Movement: The use of network segmentation can effectively stop lateral migration. A security plan for a company should have several authorization checkpoints for key resources. Attackers hiding in the network are prevented from accessing critical resources by special checkpoints.
In addition, a security analyst can utilise Log360, which has machine learning capabilities, to identify unusual activities. Computer systems may be designed to recognise anomalous behaviour using machine learning. The accuracy of identifying threats is considerably increased by using these strategies in cybersecurity. Additionally, machine learning may be taught to ask preliminary questions about risks that have been identified, reducing the frequency of false positives in security systems.
- Protection from Data Exfiltration: The risk of data exfiltration can be reduced by limiting the access points to sensitive information. This entails turning on ports and communication channels just when they’re needed and keeping them off at other times. Access to data must be controlled, monitored, and restricted to those personnel who actually need it.
Security analysts may better identify which users are utilising external storage media and on which devices by using the thorough information on detachable disc activity that Log360 offers. With an easy-to-use interface that offers detailed, thorough, and useful information on all areas, Log360 assists in keeping track of significant actions occurring in Microsoft Exchange Servers.

The Irish Log360 Experts
We hope this post gave you some insight into how MITRE are helping businesses stay safe from cyber threats. When used in conjunction with Log360 from ManageEngine you’ll be securing your business assets online. We are the leading experts in Ireland when it comes to Log360 – be it for setup, training or consulting – and have been providing Log360 services to our clients for years. If you have any questions about IT Security then make sure to contact us.
If you have an IT Problem then we’ve got the IT Solution, call us on +353-1-2304242 or contact us online for more info!




