One unquestionable fact about an increasingly digitalized world is that cyberattacks are still a constant threat. It is critical that we arm ourselves against the incoming wave of cybercrime as we enter the new year.
What is Cyber Threat?
A cyber threat, or cybersecurity threat, denotes any malevolent action aimed at pilfering, compromising, or impairing data integrity, thereby jeopardizing the digital equilibrium and security of an organization. Within the spectrum of cyber threats lie a diverse array of assaults, spanning from data breaches and computer viruses to denial-of-service attacks and an array of other nefarious tactics. This discourse delves into the essence of cyber threats, delineates their various manifestations, and elucidates common instances of such threats. In 2023, cybercriminals used cutting-edge technologies and a plethora of creative strategies to carry out their plans. Unfortunately, things seem just as bad for the months ahead.

The days of solely older citizens who were considered susceptible targets are long gone; nowadays, anybody may become a victim of the intricate schemes of contemporary cybercrime, which is fuelled by easily available tools and technology. A new age filled with AI-driven cyber risks was ushered in by the remarkable growth of generative AI last year.
Expert predictions indicate that cybercrime in 2024 will take on even more sophisticated and sneaky forms than in the past. As long as this clarion call is heard, awareness becomes our best line of defence. Let’s take a closer look at the maze-like world of online, where a plethora of eye-catching crimes and spectacular schemes are waiting for our cautious scrutiny.
The 3 Types of Major Cyberattacks
There are 3 main types of cyberattacks to prepare for in 2024.
1. AI-powered Cybercrime
Artificial intelligence scams are still relatively new, but they are developing at a rate that keeps up with the swift progress of AI. AI-generated films, photos, and voice reproduction have given schemes a new twist by allowing con artists to take advantage of these technological advancements and con unsuspecting people out of their hard-earned money. Phishing tactics, online shopping fraud, calls purporting to be from family members, and requests for immediate financial help have all been effective in the past. The effectiveness of AI speech frauds is demonstrated by a McAfee analysis, which shows that an astounding 77% of victims lose money. This concerning figure emphasizes the necessity of increased awareness and readiness. This year, in anticipation of the changing scene, increasingly complex AI-powered scams are expected to proliferate. Notably, job offer frauds are become more common as generative AI creates job sites and company pages that are almost identical to real ones. Simultaneously, peer-to-peer (P2P) payment scammers use state-of-the-art language models to further develop their fraudulent methods.
The crux of these matter brings in the necessity for tools like PAM360, which offer pivotal protection against cyber threats. Just as health insurance scrutinizes pre-existing conditions to ensure a secure foundation, similarly cyber insurance also mandates a good health practice in maintaining robust cybersecurity posture. organizations vying for coverage must integrate vital controls like end-to-end encryption, multi-factor authentication (MFA), and compliance with regulatory directives. The strength of these security protocols directly impacts insurance premiums. Thus, investing in PAM360 becomes imperative to shield against looming cyber threats and safeguard organizational assets effectively.
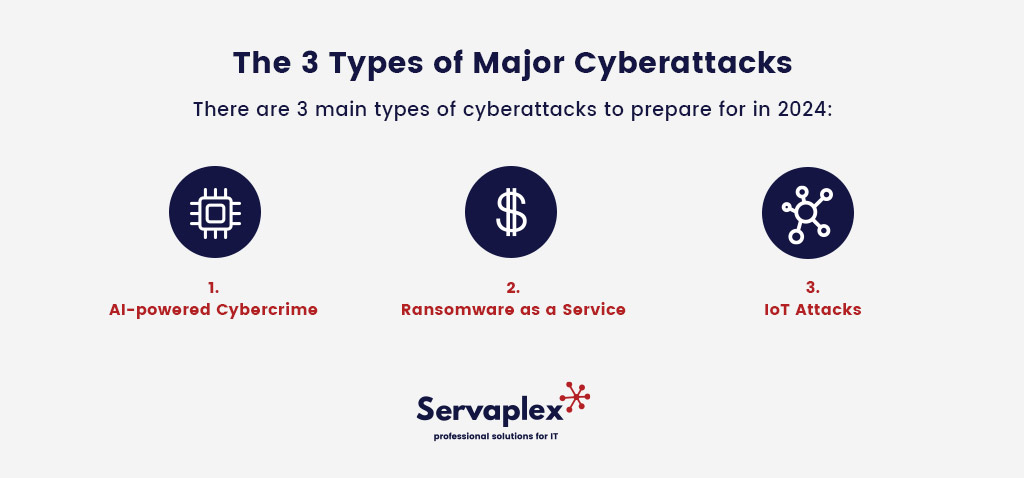
2. Ransomware as a Service
Although the idea of ransomware as a service (RaaS) is not new, it has gained significant traction in the last few years due to the increasing number of ransomware attacks. RaaS is now considered a major player in the world of cybercrime. Threat actors operating in the shadows of the dark web have the option to hire seasoned ransomware experts who can provide custom solutions made to fit their evil goals. In addition to creating personalized ransomware programs, these service providers maintain and deploy them for the criminals during their whole lifecycle.
Ransomware attacks increased by an astounding 95% in 2023 over the previous year, indicating a dire trajectory that is predicted to see a ransomware attack happen every two seconds by 2031. RaaS suppliers must always improve their technological capabilities in order to stay up with the latest developments in cybersecurity, as this concerning trend emphasizes. It is critical to protect your company with cutting-edge anti-ransomware software to prevent these kinds of attacks and prevent your business from suffering potentially disastrous financial losses.
3. IoT Attacks
The Internet of Things (IoT) is quickly becoming a household name as 5G technology takes centre stage in cellular connectivity. This ushers in a new era of interconnectedness but also presents a plethora of vulnerabilities. By 2024, the Internet of Things (IoT) has grown to include a wide range of commonplace necessities, from industrial machinery, medical infrastructure, and automobiles to home security systems and appliances.
The Internet of Things (IoT) comprises three distinct attack surfaces: the device itself, the communication channels it uses, and the software infrastructure that underpins it.
IoT device vulnerabilities are frequently caused by incorrect factory default settings or defective hardware, like memory or firmware, which can be easily abused by hostile actors if they can be shown to be old or weak. Maintaining device security requires regular firmware updates, and applying security patches as soon as manufacturers release them is crucial for addressing known vulnerabilities. Staying up to speed with these updates guarantees that your IoT environment will continue to be resistant to new threats.
Additionally, because IoT devices are interconnected, there is a greater range of vulnerabilities and a larger attack surface due to the communication routes that connect them. Adopting strong cybersecurity measures can greatly reduce vulnerabilities and improve the overall security posture of your Internet of Things ecosystem. These methods include device authentication, data encryption, and network security protocols like firewalls.
Moreover, the apps used to communicate with Internet of Things devices offer an additional channel that is vulnerable to cyberattacks. The main entry points for Internet of Things threats include weak passwords and insufficient authentication protocols. Adopting tools like password managers helps create strong passwords and store them safely to avoid security breaches. Furthermore, by providing authentication and encryption methods, cloud security solutions are essential in reducing risks and strengthening the resistance of your IoT infrastructure against malicious incursions.

Identity 360
Identity360 from ManageEngine is a powerful instrument that helps strengthen your cybersecurity defences. This platform, which is specifically built to tackle the constantly changing cyber threat scenario, provides an extensive feature set aimed at risk reduction and asset protection. Get your Identity360 and secure your IT resources right now, to know more contact us.
If you have an IT Problem then we’ve got the IT Solution, call us on +353-1-2304242 or contact us online for more info!